Windows Admin Center (WAC) ACME certificates with PFsense

In this guide I will show you how to setup automatic certificate renewal for Windows Admin Center (WAC) with the PFsense ACME package. The starting requirement for this guide is that you have already setup the ACME solution within PFsense, if not you can use This guide.
Creating a certificate user
- First navigate to this github script I created and download it to your Windows Admin Center instance.
- Second you should create a custom Pfsense user with restricted access, do this by going to System -> User Manager -> Add. After that, create a user and name it accordingly.
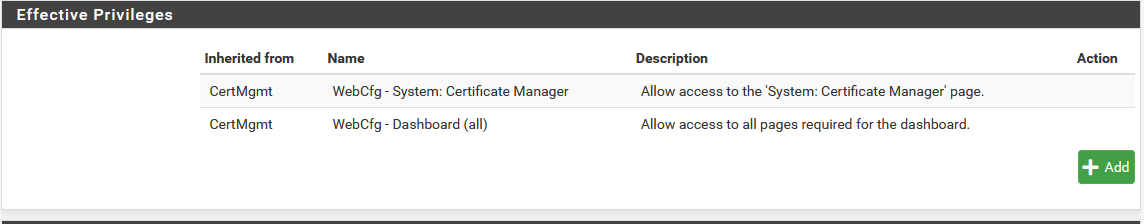
- After creating the user, you should create a PFsense group to assign this new user to. In addition, edit the group to assign correct privileges. Under assigned privileges add WebCfg - System: Certificate Manager and WebCfg - Dashboard (all). Set the variable
$PFSENSE_USERNAMEand$PFSENSE_PASSWORDin the script for the certificate user we have created and change the$SITEvariable to the FQDN or ip-address of the PFsense instance.
Setting the certificate variables
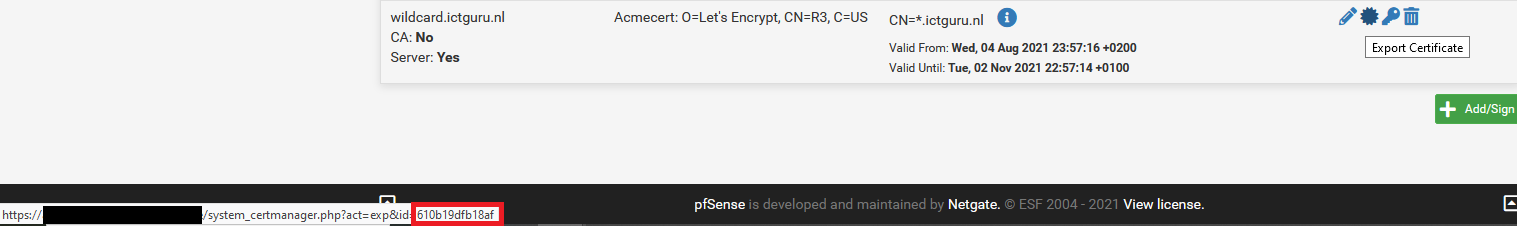
- Head to System -> Certificate manager -> Certificates. You should hover over the export certificate button of the certificate you’ll want to enroll for your WAC instance. We are looking for the certificate id, this is the red string in the screenshot. Set this as value for the
$CERTIDvariable. - In addition we should set the following variables.
$CERTNAMEwill be the name for your certificate once downloaded,$CERTDIRis the location where the certificates will be downloaded and merged into a .pfx file.$PFXPASSWORDis the password that will be set for your certificate file and$WACPORTis the port on which your Windows Admin Center instance will be running.
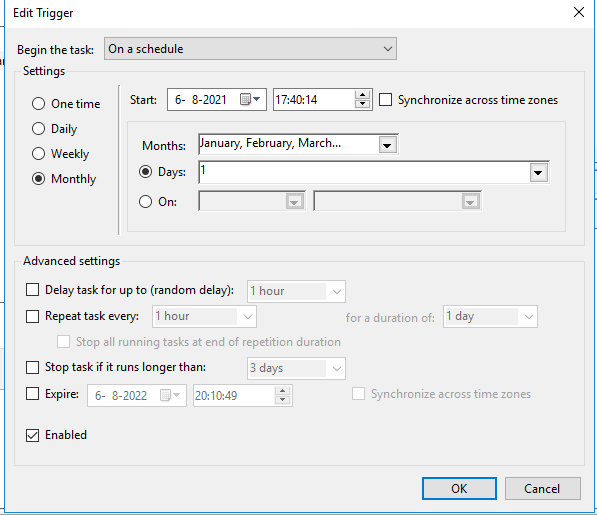
Creating the scheduled task for automatic renewal
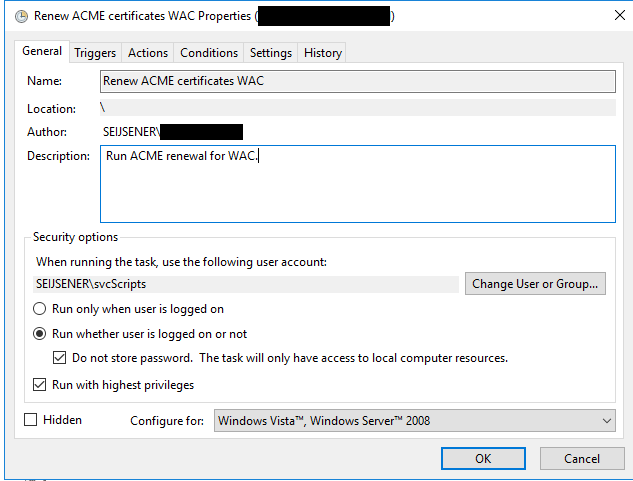
After that, we can create scheduled task on the WAC server. Preferably a service account with administrative privileges for running the script. Create the scheduled task according to the screenshots below, for running script i recommend setting the program to powershell.exe and the arguments to -NoProfile -NoLogo -NonInteractive -ExecutionPolicy Bypass -File c:\PfsenseACME-WacSSL.ps1
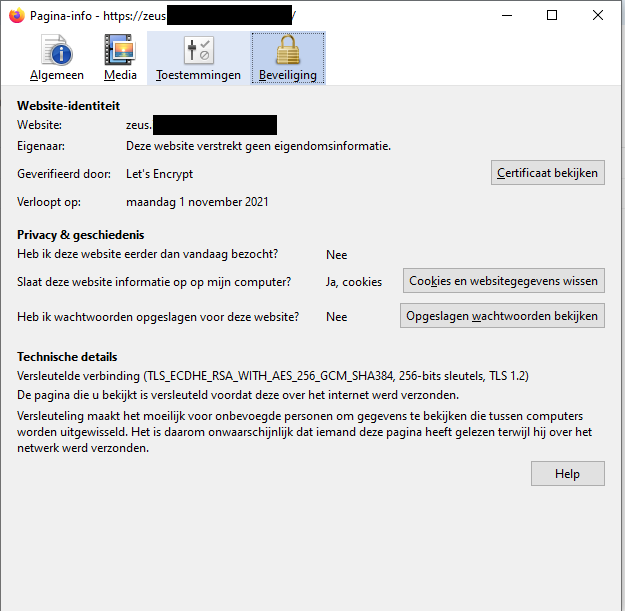
Test the scheduled task that you have created above and check the results by going to your WAC server in you browser. After that, you should be greeted with a smaal green lock inside your web browser. And just like that, automatic, valid and free certificates deployed inside your network on Windows!